Information Security and IT Security
Why is Information Security so important for companies?
Information security is becoming increasingly important, especially in the face of increasing cybercrime. Security must be taken very seriously, otherwise the consequences will be unpredictable. Extortion, theft of personal or business data and the failure of IT services have major economic consequences. We therefore advise you comprehensively on all questions and issues relating to information security.
- Proactive Consulting
- Highly networked in the industry
- High level of expertise
- Focused solutions
- Dynamic and agile team
Our security experts are glad to consult you!
We help you reach your individual project objectives.
ISO 27001 Consultancy
Would you like to be certified according to ISO 27001 in the medium or long term? We support you in setting up an ISMS according to ISO 27001 and help you prepare for an audit.
The ISO 27001 standard describes the specific requirements for the establishment, implementation, maintenance and continuous improvement of the documented information security management system. This standard also specifies requirements for the assessment and treatment of information security risks, adapted to the individual needs of the organisation.
Cooperation Process
- Proposal and initial interview. We then create an offer and a possible project plan.
- We arrange the first dates for workshops and set up a Jour-Fixe.
- Gap analysis
- Development of potential management processes
- Development and monitoring of risk management
- Preparation and coordination of directives
- Project planning and management
- Conduct of internal audits
- Monitoring of external audits
- Individual examination of individual subject areas
- Sensitization
TISAX® Consulting
We support you in setting up an ISMS according to TISAX and help you prepare for an audit. TISAX ‒ the 27001 of the automotive industry.
The TISAX®* test standard stands for reliable quality and a common level of safety in the automotive industry that is recognized by all manufacturers worldwide. For many car manufacturers, a valid TISAX® label is already a prerequisite for cooperation with suppliers and service providers. The TISAX® requirements combine industry and customer standards, reduce costs, effort and complexity and create the greatest possible transparency and security for you as a supplier.
*TISAX® and ENX® are registered trademarks of ENX.
Cooperation Process
- Request and initial interview. Afterwards, we will prepare an offer.
- Analysis of the CAP
- Determination of maturity
- Consulting and development of ISMS
- Sample documents
- Preparing for audits
- Follow-up by audits
Establishment and Operation of an Information Security Management System (ISMS)
We support you in setting up and developing an ISMS ‒ up to certified information security.
With the help of an ISMS, the complex tasks of controlling safety-relevant processes in a dynamic environment of an organization are designed and presented in a user-friendly way. This increases the security level of an organisation, reduces risks and creates competitive advantages. Compliance with legal requirements as well as voluntary and/or prescribed safety standards is paramount.
Cooperation Process
- Request and initial interview. Afterwards, we will prepare an offer.
- Advice and support in setting up an ISMS
- Support during commissioning of the ISMS
- Annual monitoring
- Maintaining the ISMS
In order to optimally prepare our customers for information security and to implement compliance management in a comfortable and resource-saving manner, we are now cooperating with Akarion.
Penetration Test (Pen Test)
Perform Pentest now and identify IT security vulnerabilities.
We scan your application, infrastructure or hardware for security vulnerabilities and uncover potential threats and unknown vulnerabilities using a planned attack.
Our day-to-day business is to test the IT systems of organisations of different sizes. From infrastructure to web applications to interfaces. We work independently of manufacturers and suppliers and therefore contribute holistically to increasing the level of IT security.
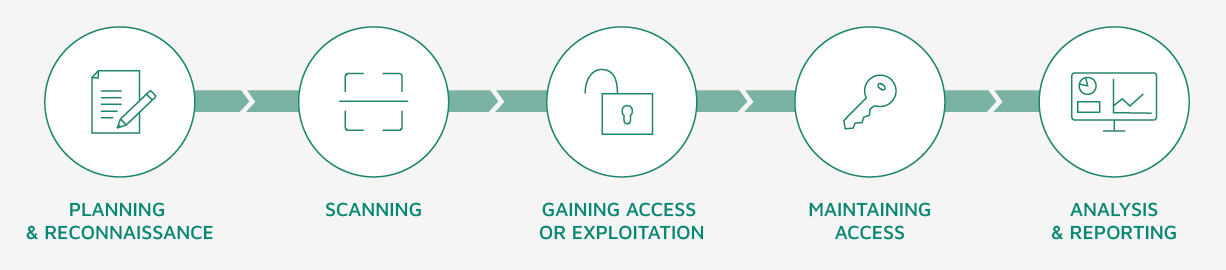
Cooperation Process
- Inquiry
- Preliminary discussion and clarification of objectives. Afterwards, we prepare an offer and a possible project plan.
- Performing pen tests. If critical vulnerabilities are detected, we will notify you immediately.
- Documentation and presentation of results
- Support for the implementation of the recommended measures
Would you like to increase your information security in practice? You have to perform a penetration test due to external requirements? Then contact us now without obligation. We will prepare an individual offer for you as soon as possible.
Incident Response Management (IRM)
Do you need assistance in drawing up a plan to deal with hazards?
An incident response is the response of an organization to an IT security incident, such as a cyber attack.
With the help of Incident Response Management, organizational and technical measures are developed to best prevent and contain the incident in order to keep the damage as low as possible.
Cooperation Process
- Inquiry and initial interview. Afterwards, we will prepare an offer.
- Creation of an Incident Response Plan (IRP)
- Preparing for potential incidents
- Identification and containment of security incidents
- Advice on the recovery of affected systems
- Incident documentation and analysis
- Training
Business Continuity Management (BCM) / IT Emergency Management
We support and advise you in setting up an effective IT emergency management.
With established business continuity management, you increase the resilience of your company and thereby create a scope for action and options in case of an emergency. The prepared restart plans will bring you back to the ability to act as quickly as possible and secure you a decisive competitive advantage.
Cooperation Process
- Inquiry and initial interview. Afterwards, we will prepare an offer.
- Establishment of a risk management system
- Development of emergency concepts for emergencies
- Recovery plan for critical business processes
- Reduction of costs due to downtime
- Preserving legal certainty in the event of an emergency
Social Engineering
We would be pleased to explain the different types of social engineering to you in a personal interview and find the right product together with you.
Social engineering refers to the manipulation of people to gain confidential information or access to certain resources. The term refers to techniques by which attackers exploit human vulnerabilities such as curiosity, greed or trust. Social engineering can be done in different ways, such as phishing emails or personal contact with a victim. In order to protect yourself, it is important to be attentive and sceptical and not to pass on confidential information without verifying its authenticity.
We offer, among others, the following services
- Phishing
- Spear Phishing
- Voice Phishing
- Smishing
- USB-Dropping
- Physical Intrusion Test
- Training / Awareness Raising
- and many more…


























